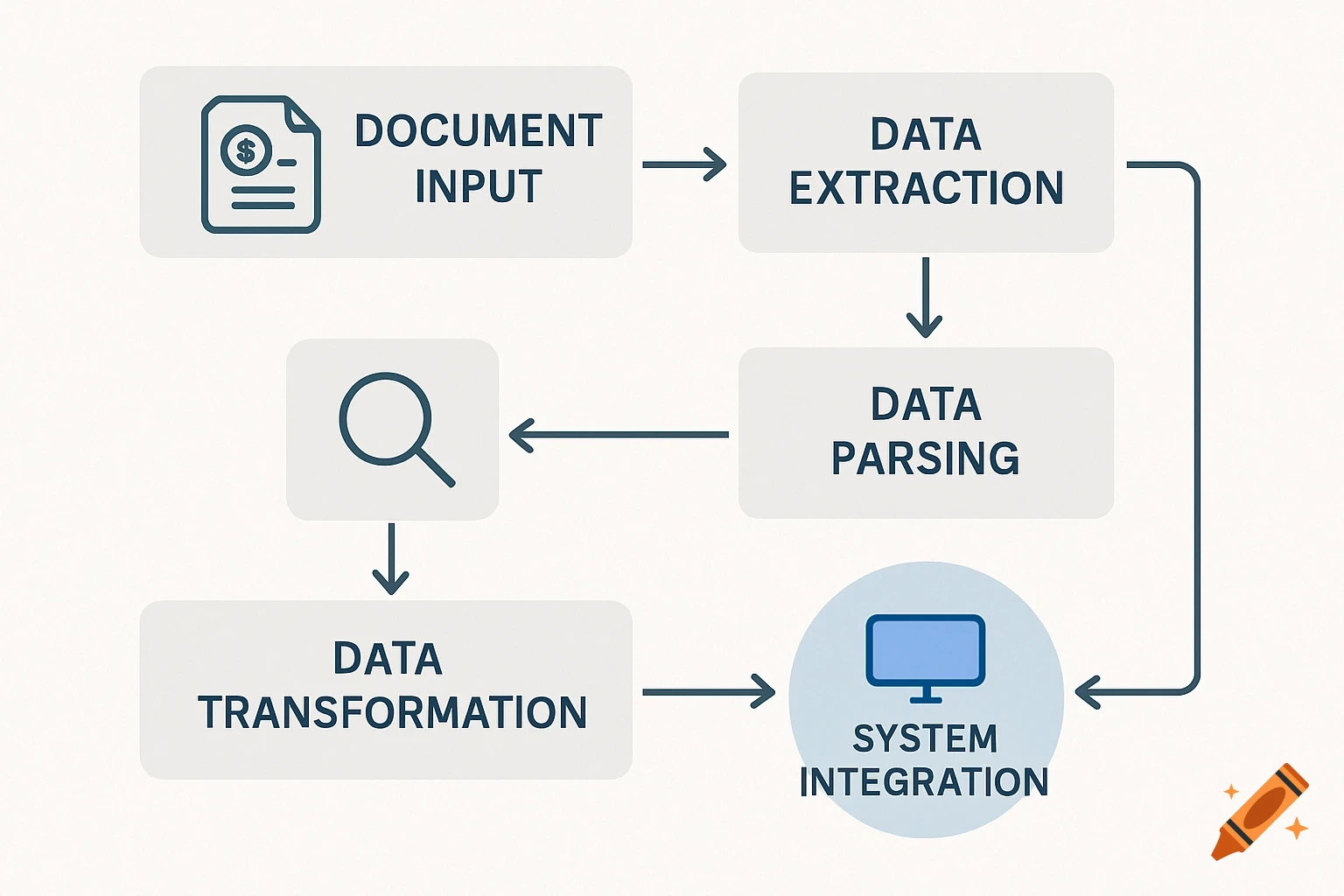
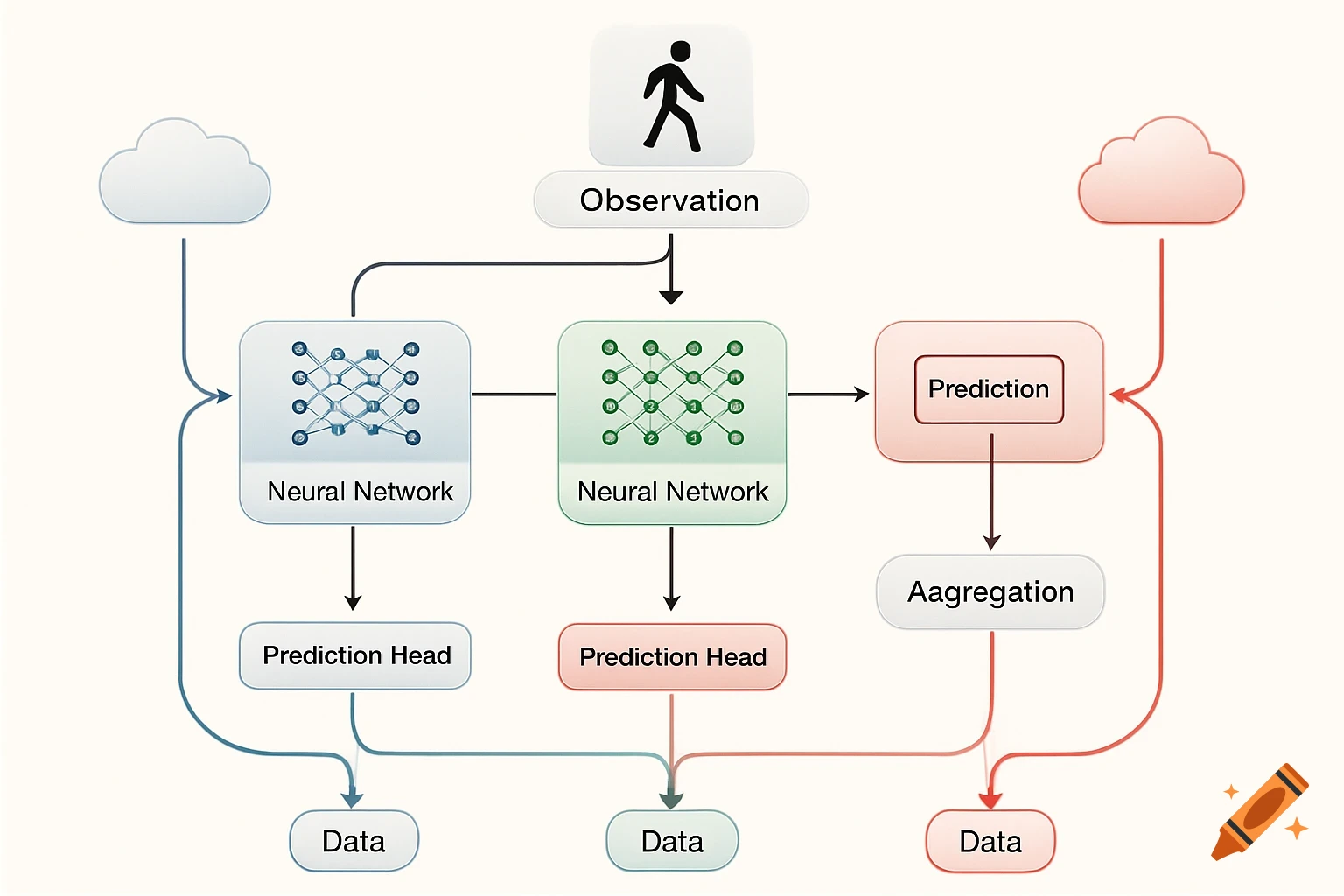
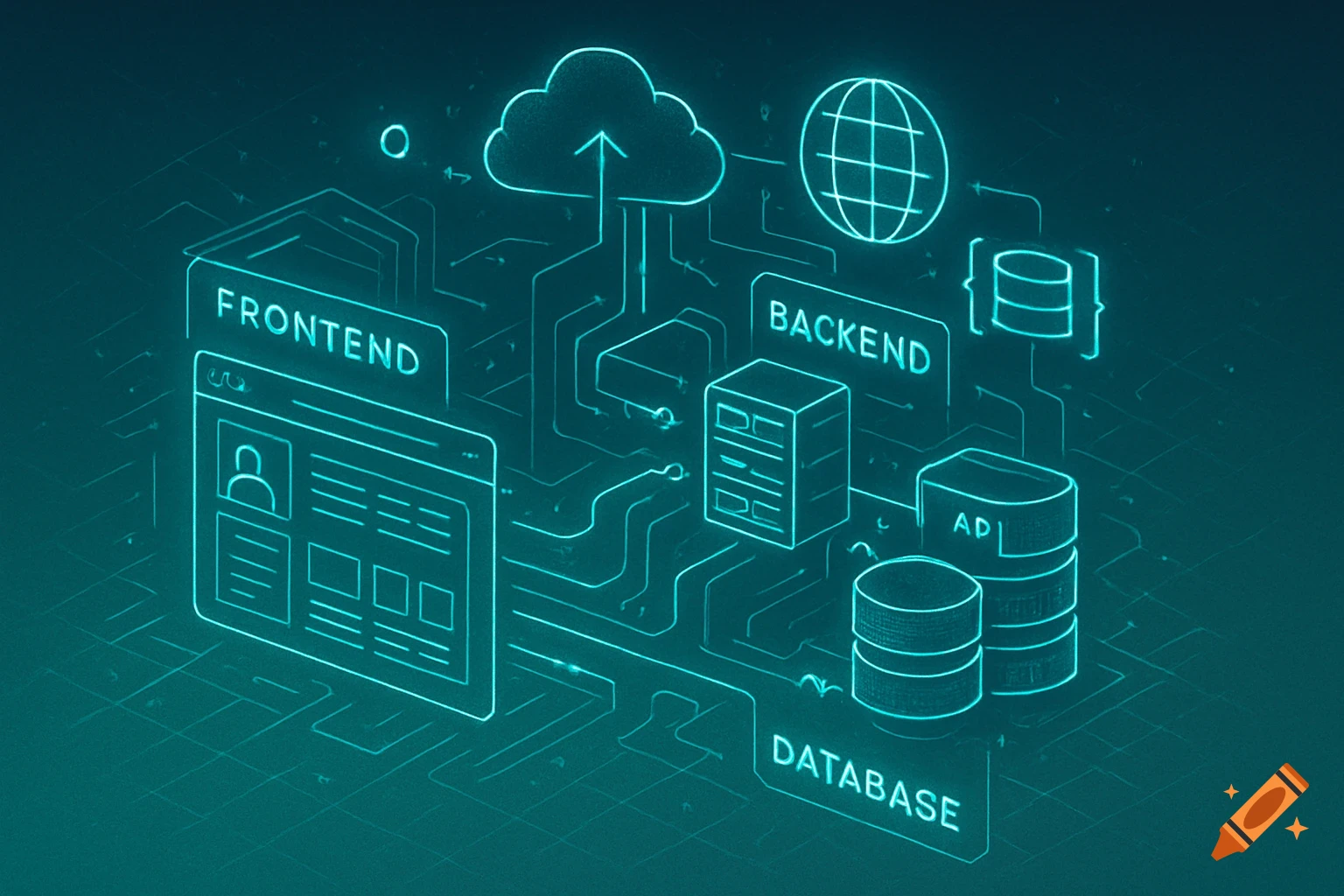
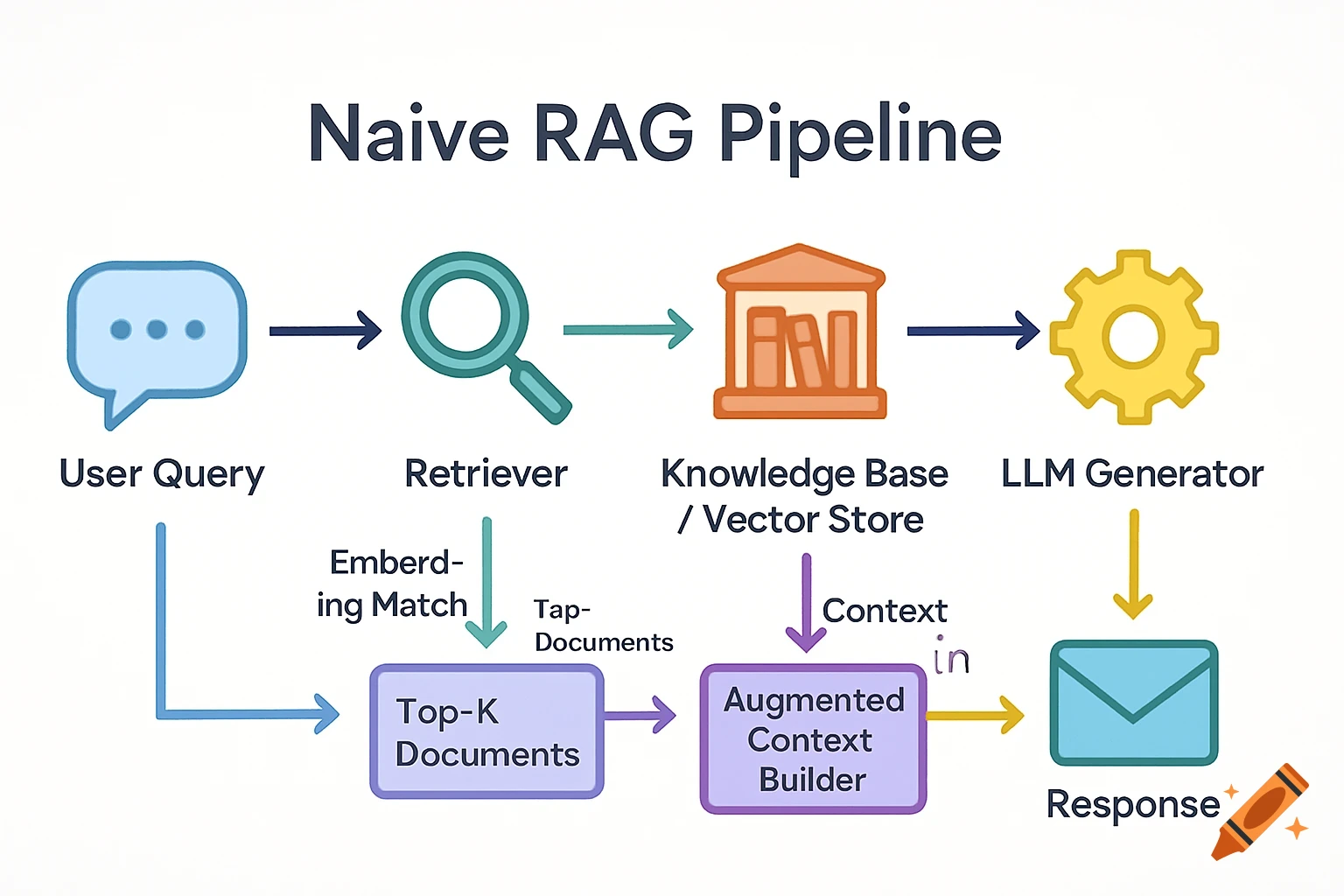
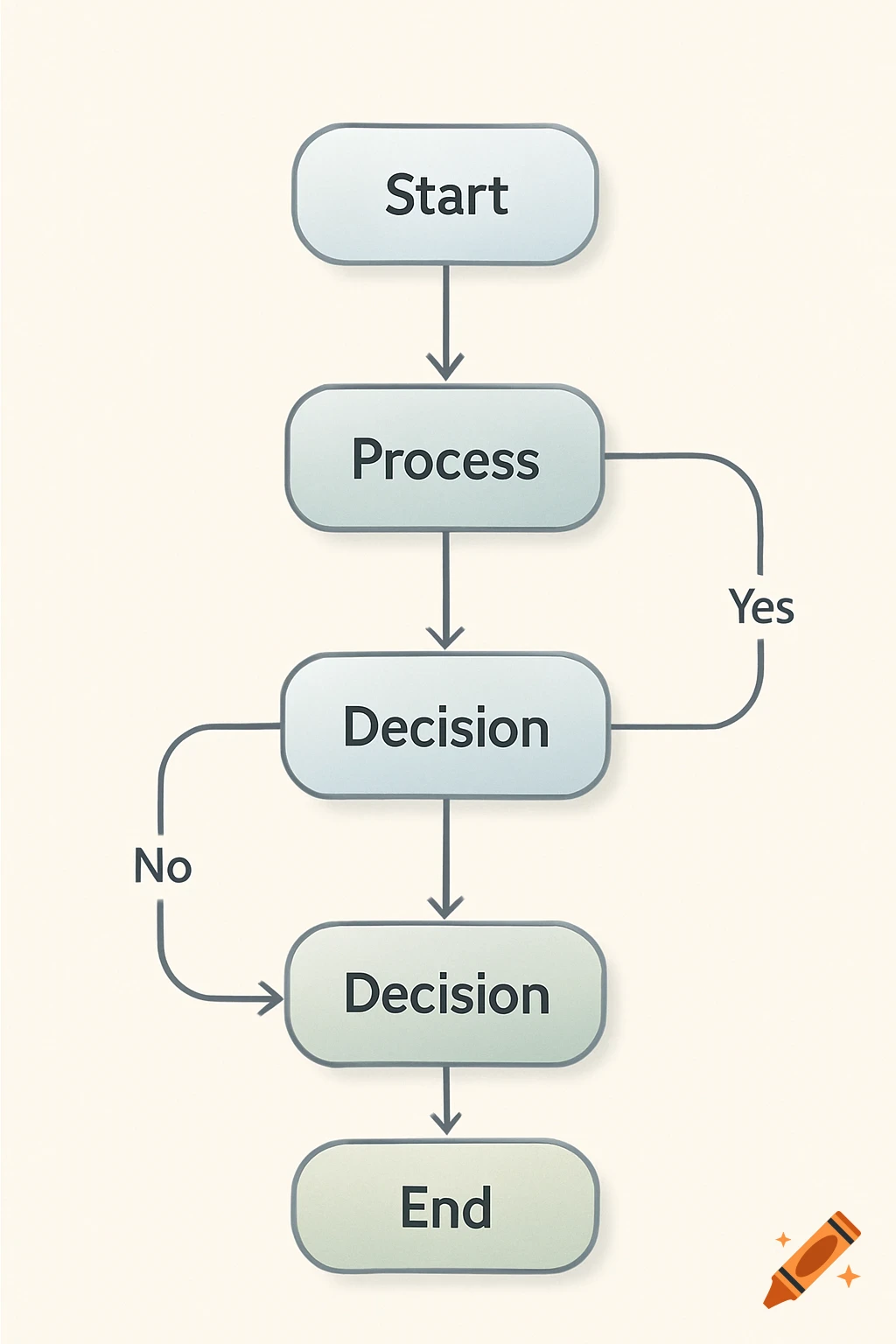
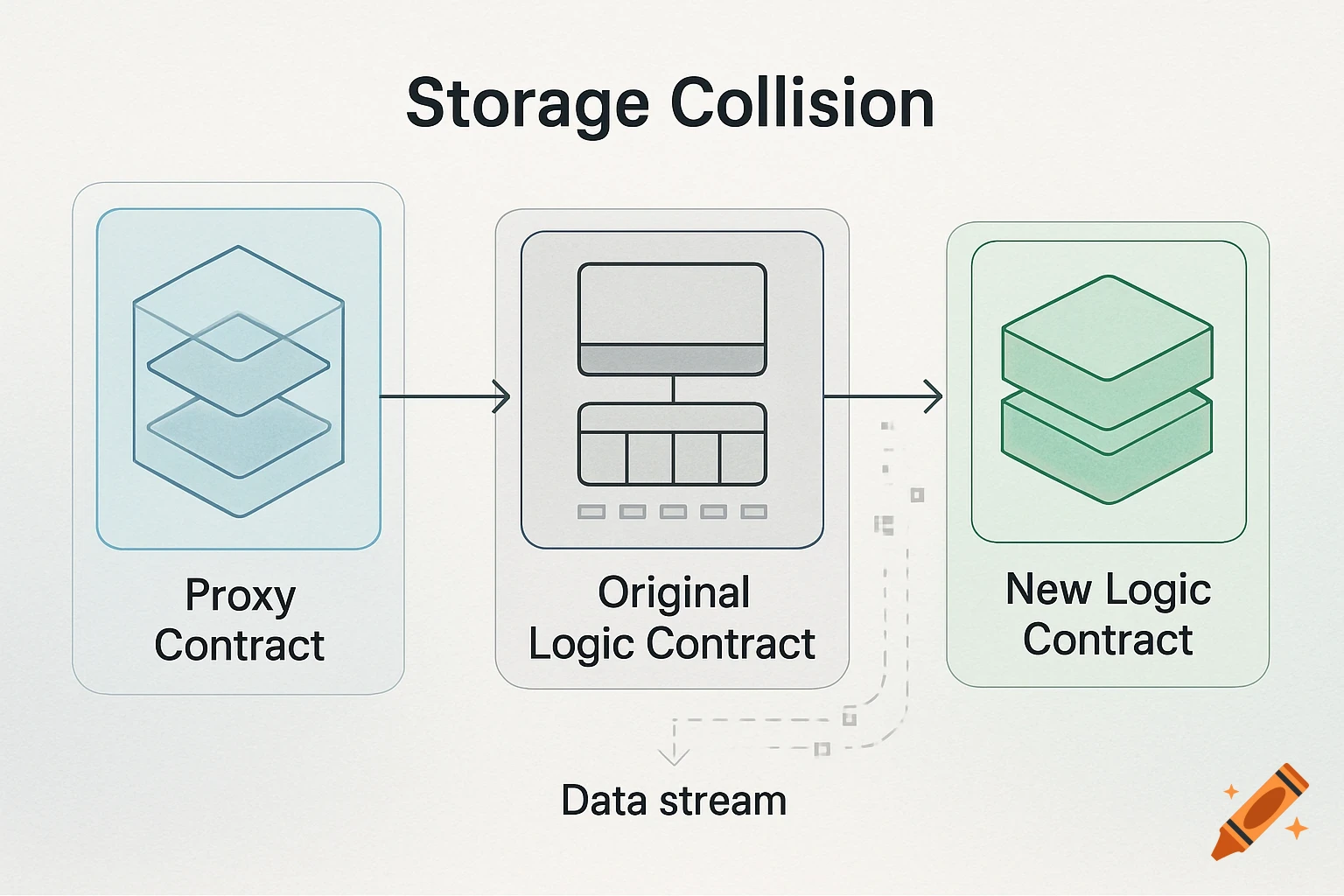
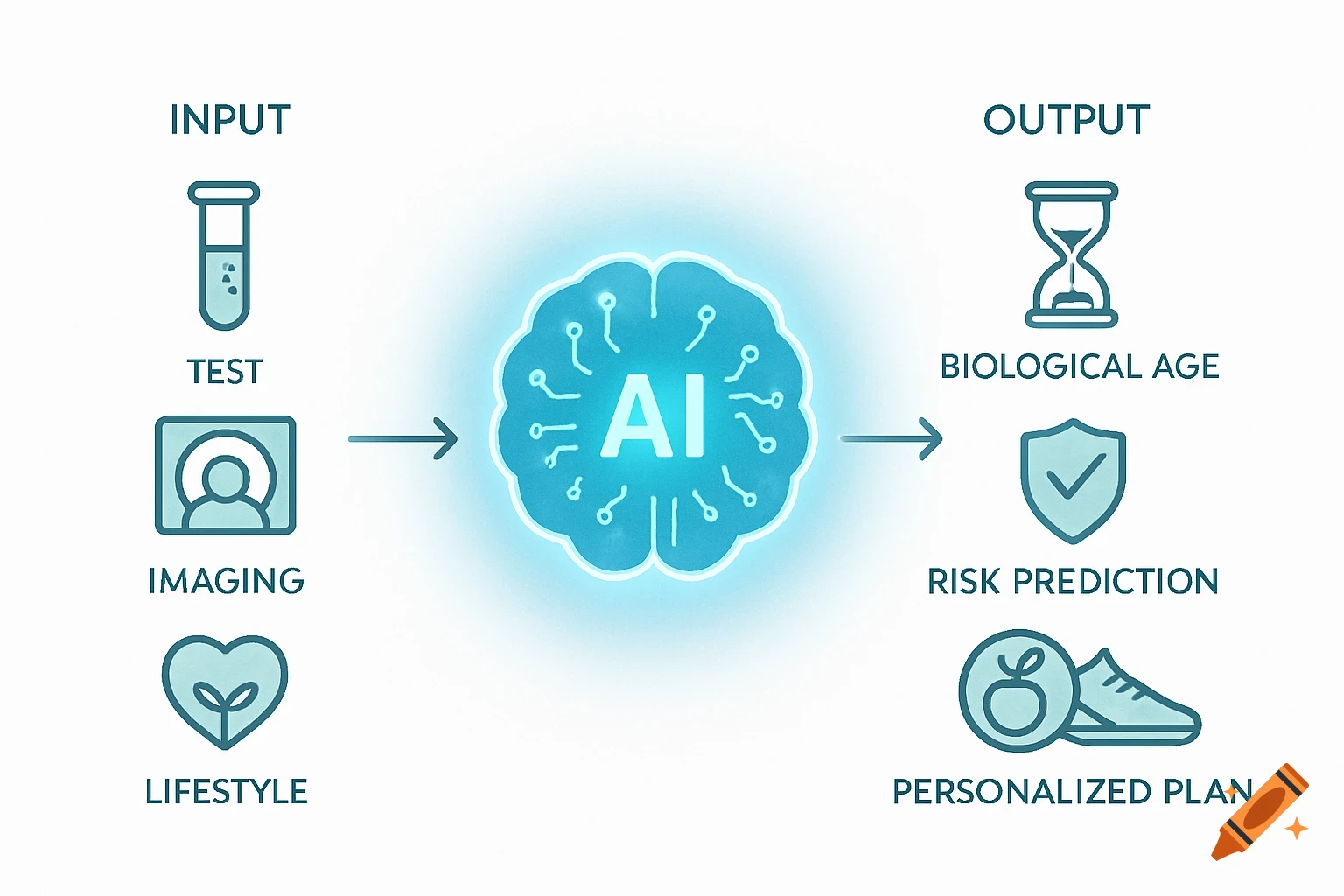
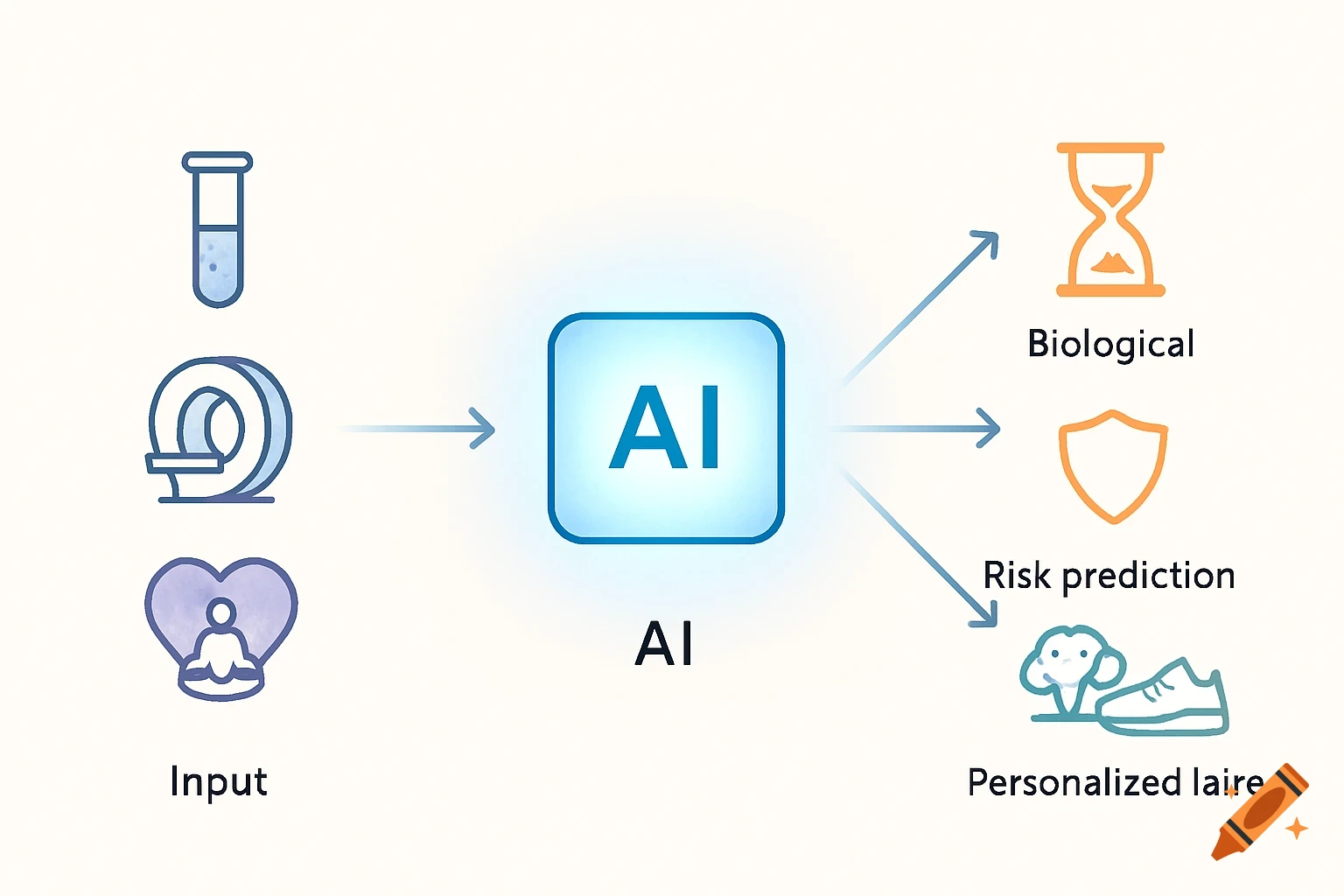
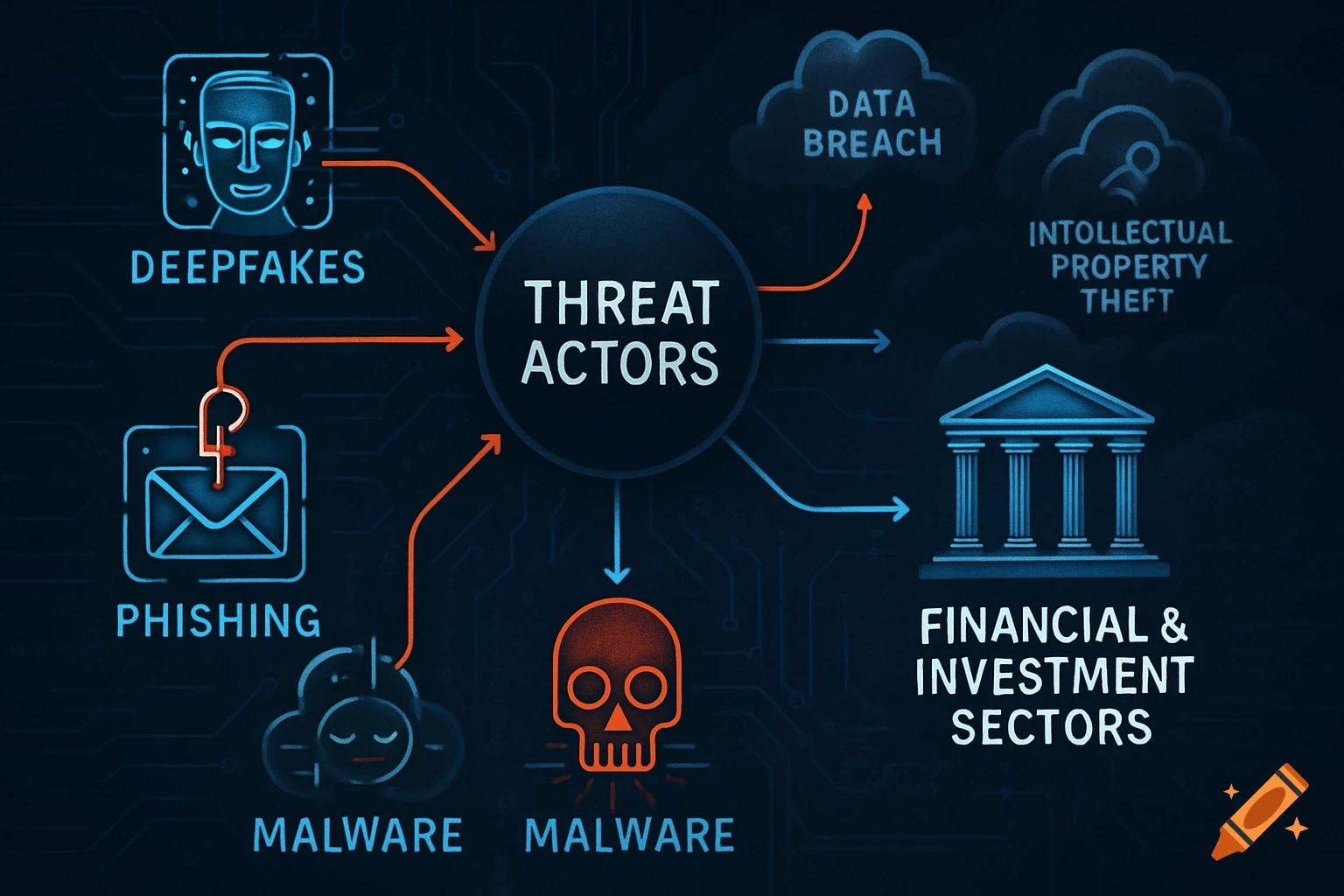
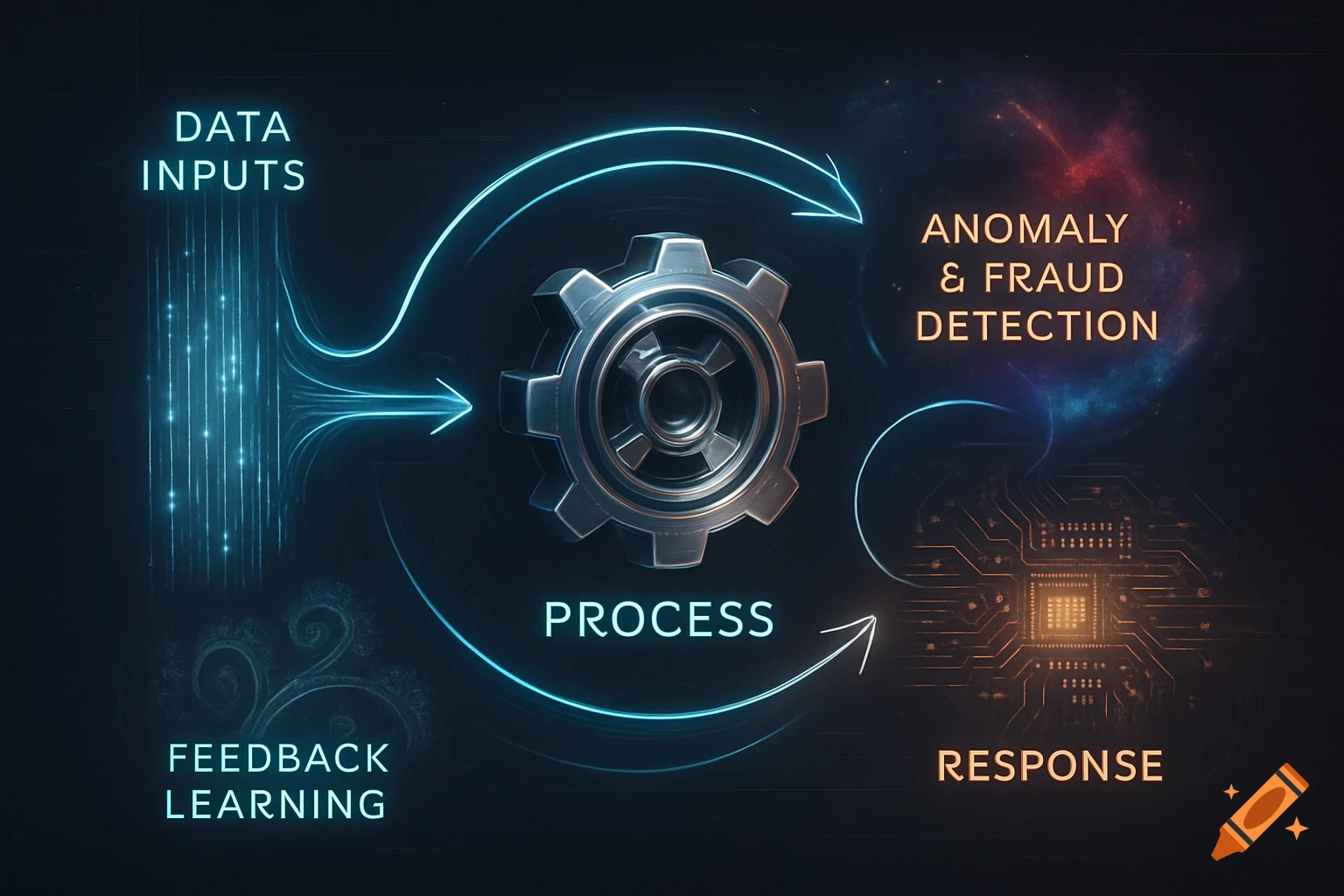
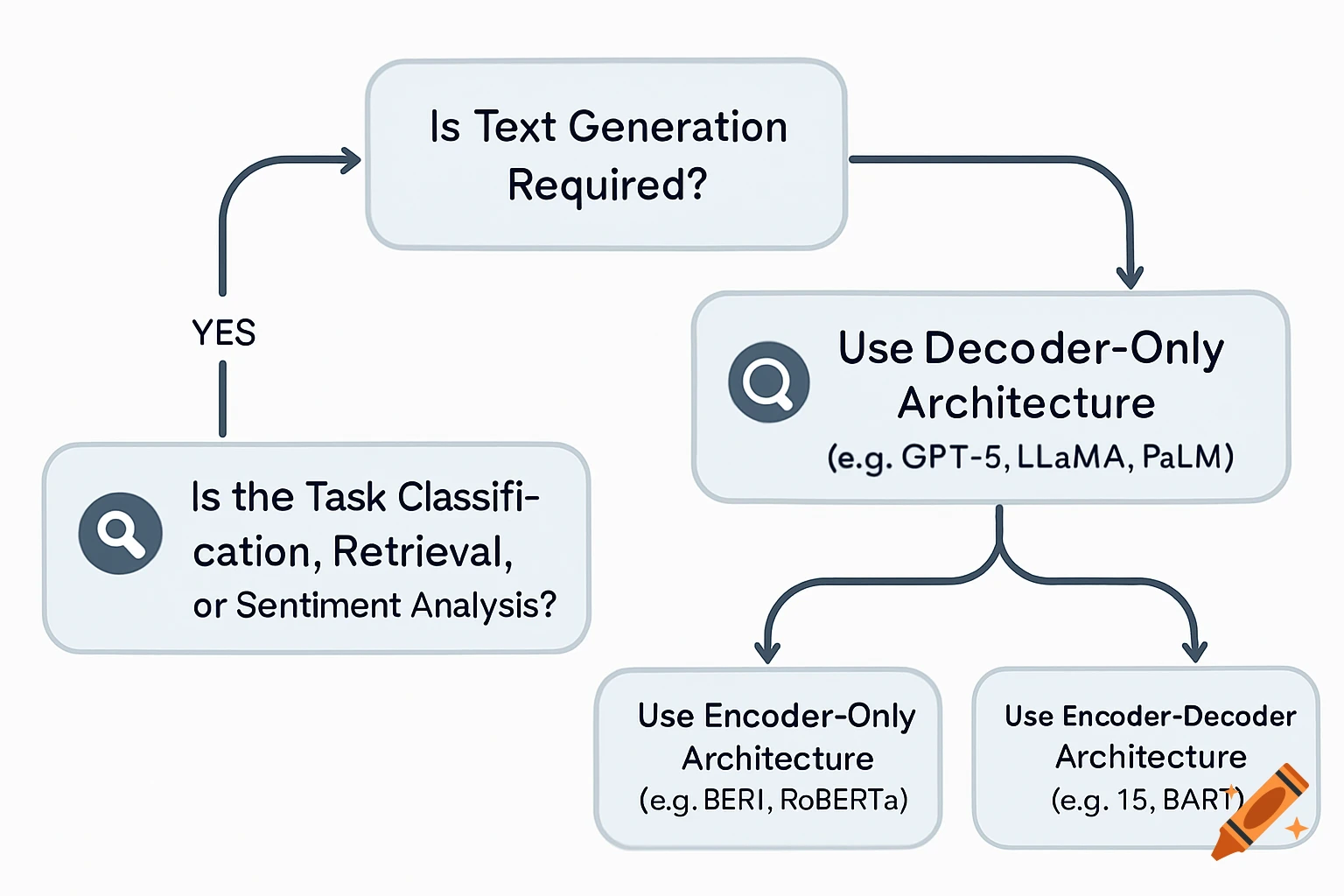
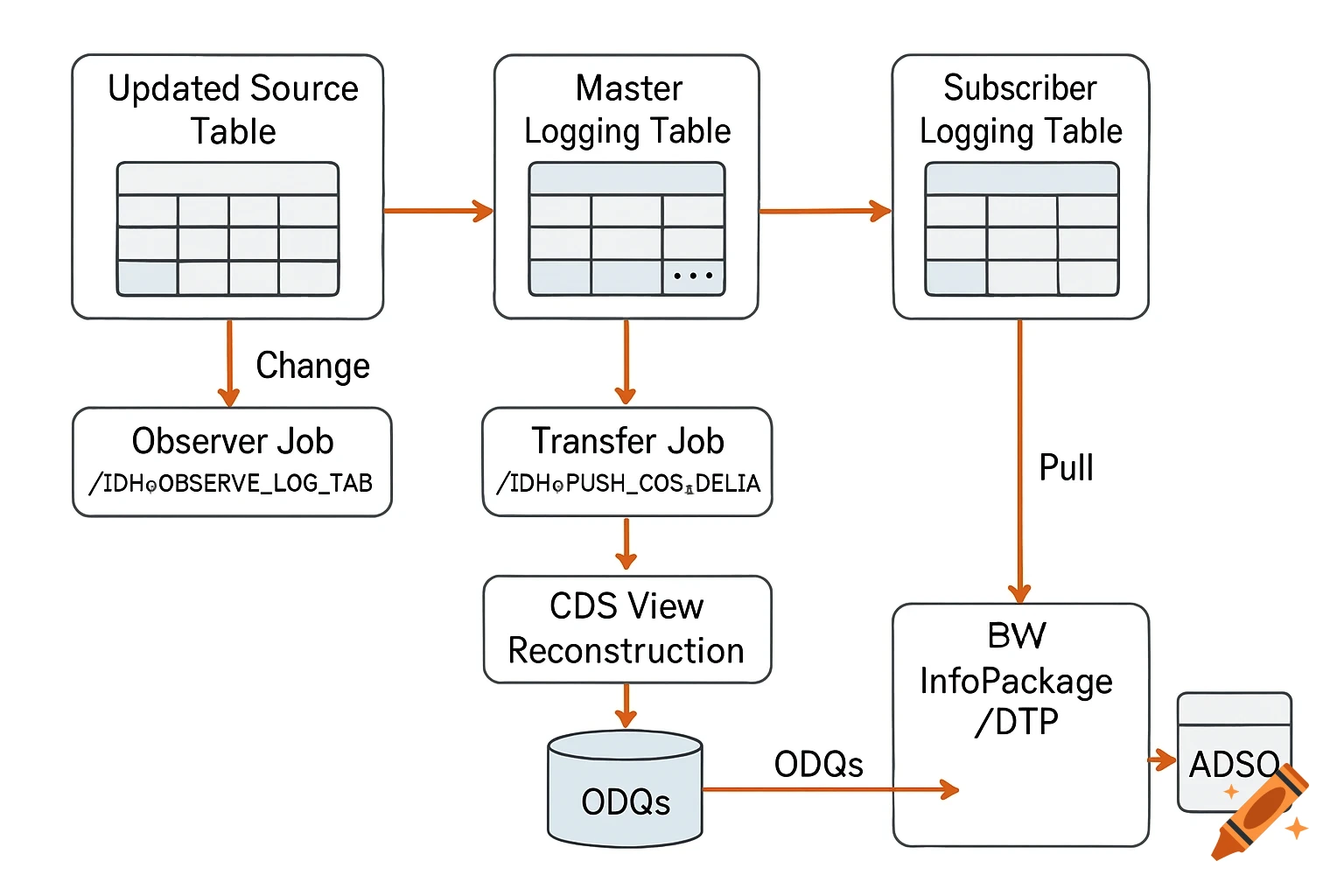
A flowchart detailing an AI threat detection process, starting with network data, through analysis, threat assessment, and STIG-based response.
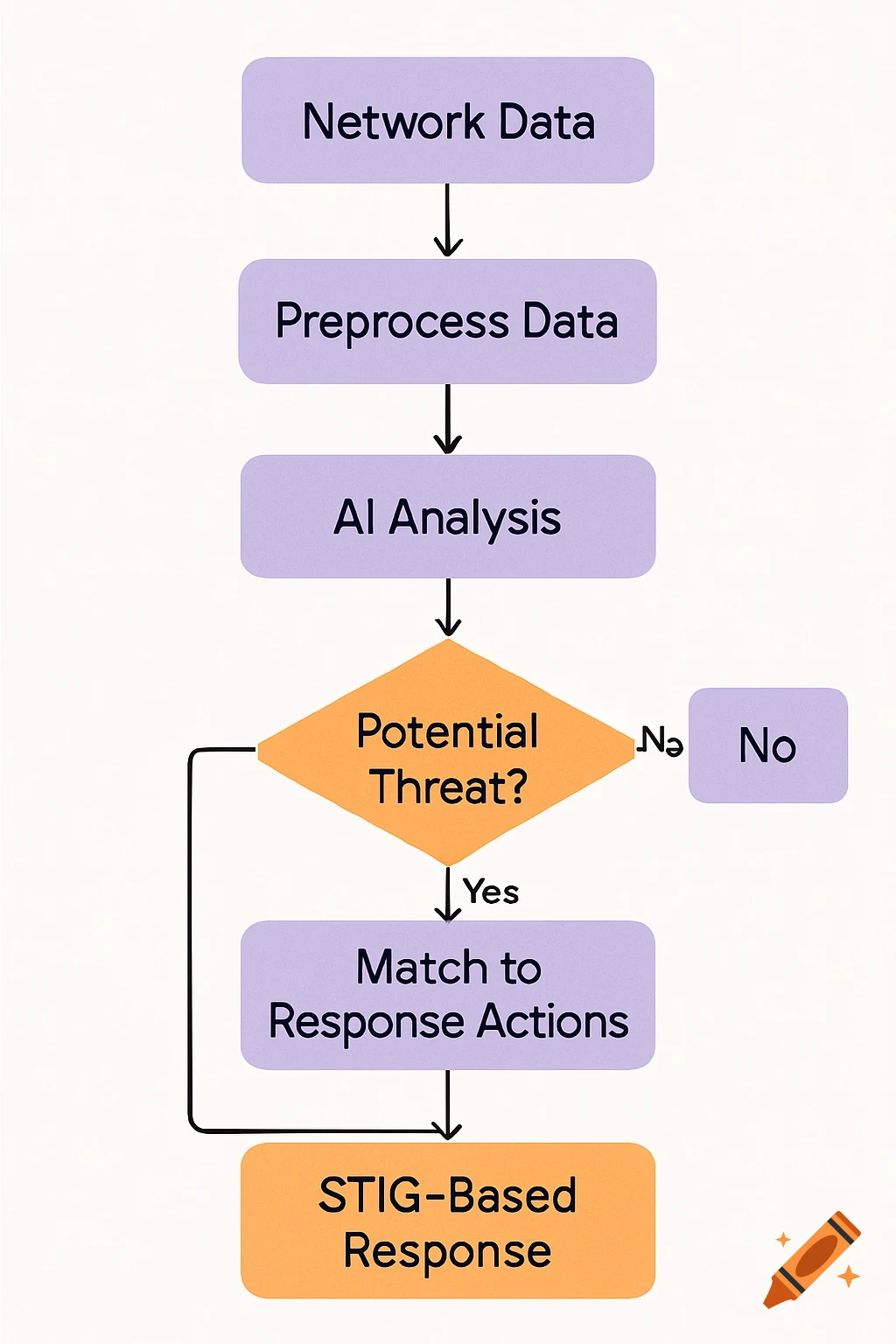
AI Threat Detection Flowchart This flowchart shows the step-by-step process of how the AI system would analyze network data, detect potential threats, and match them to the correct STIG-based response actions. It helps explain the logic behind the AI decision-making and is key to understanding the system design described in the project. See more