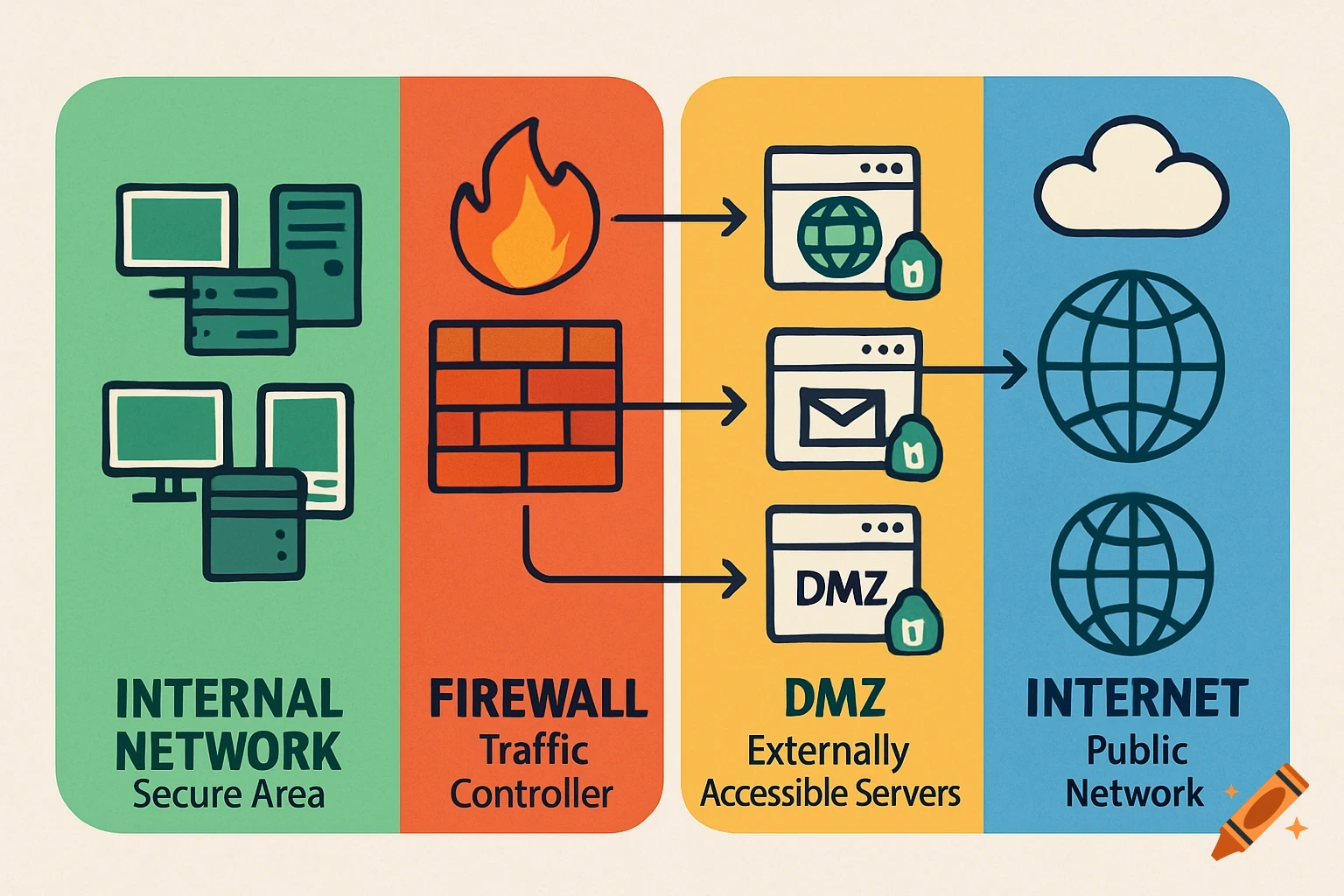
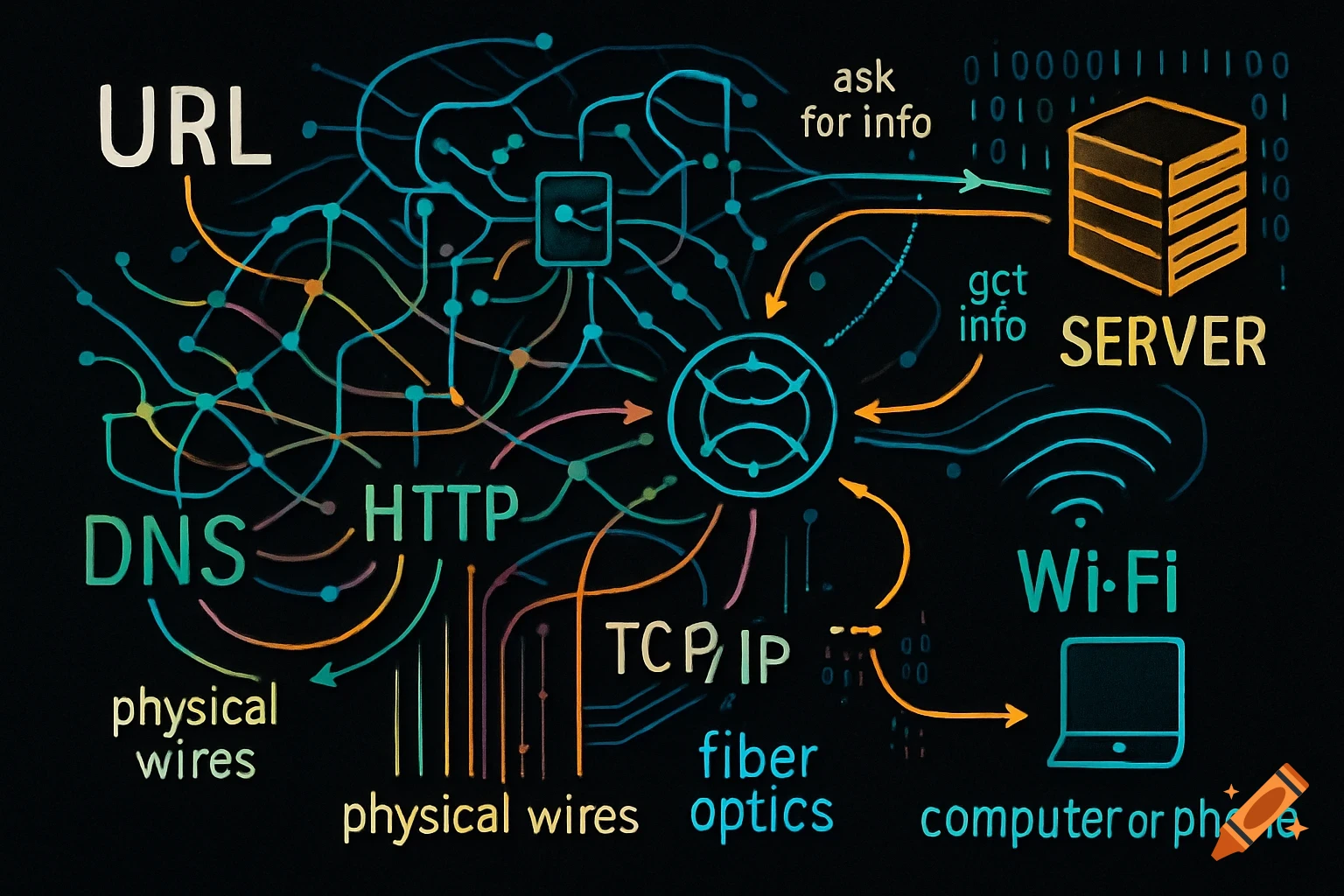
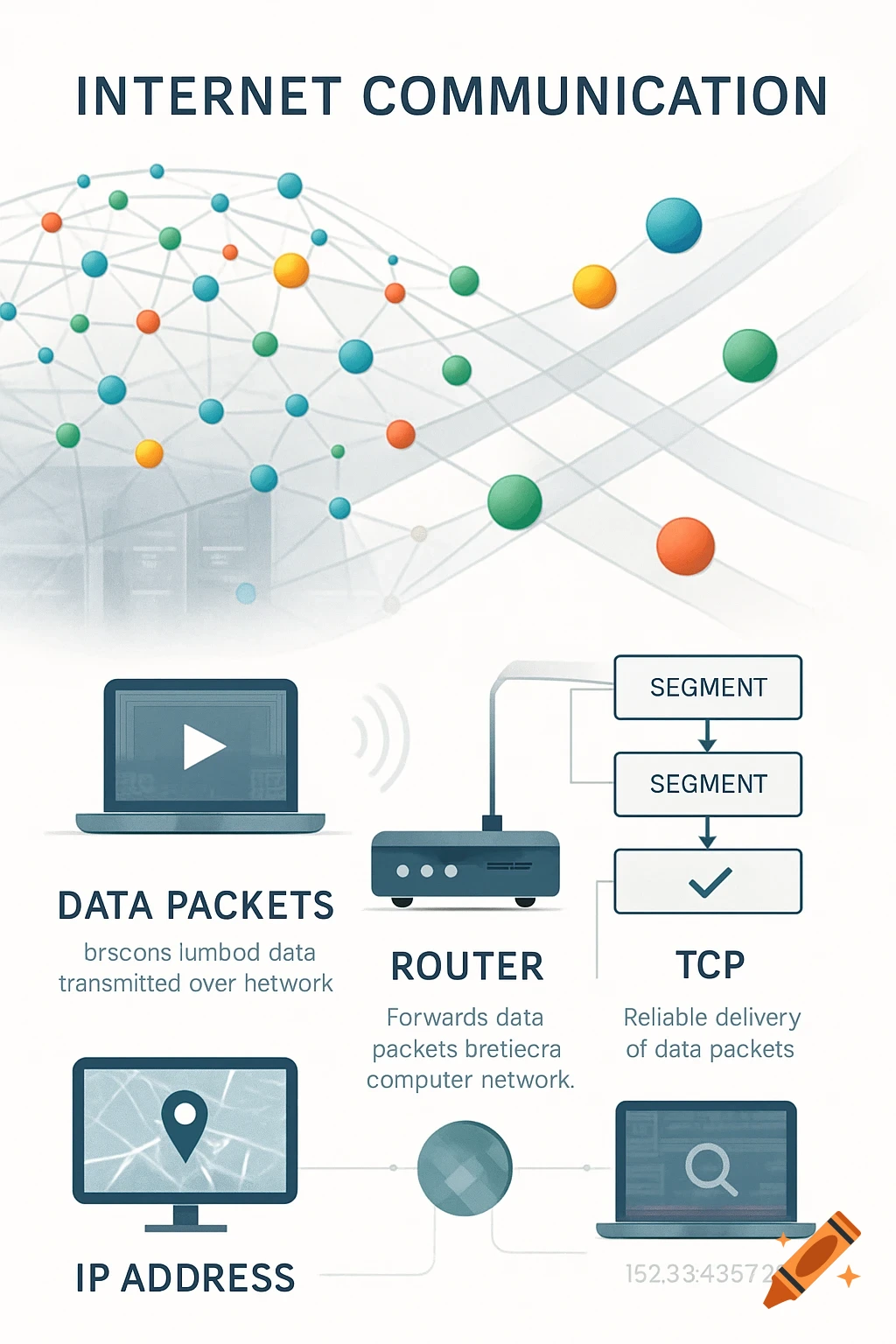
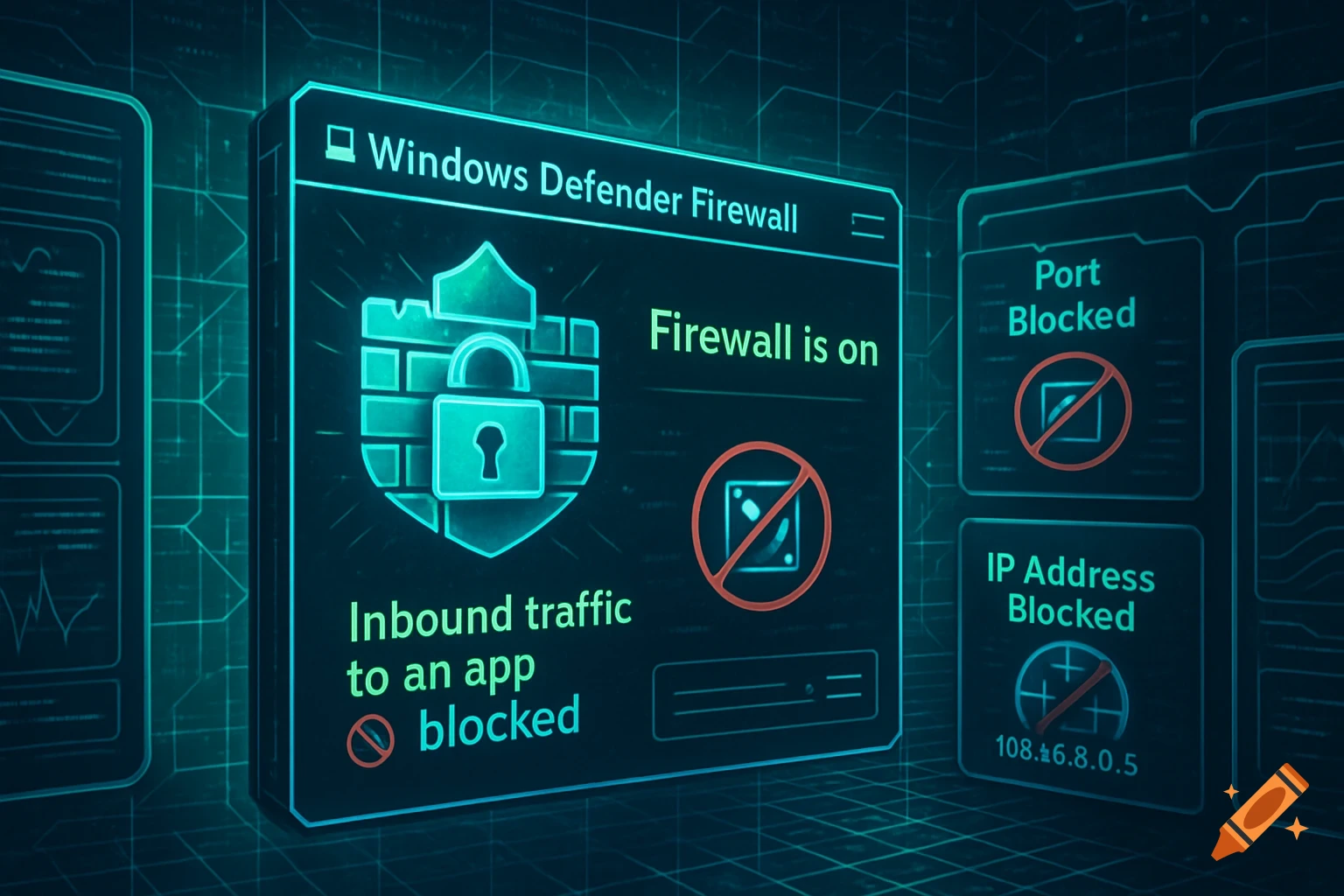
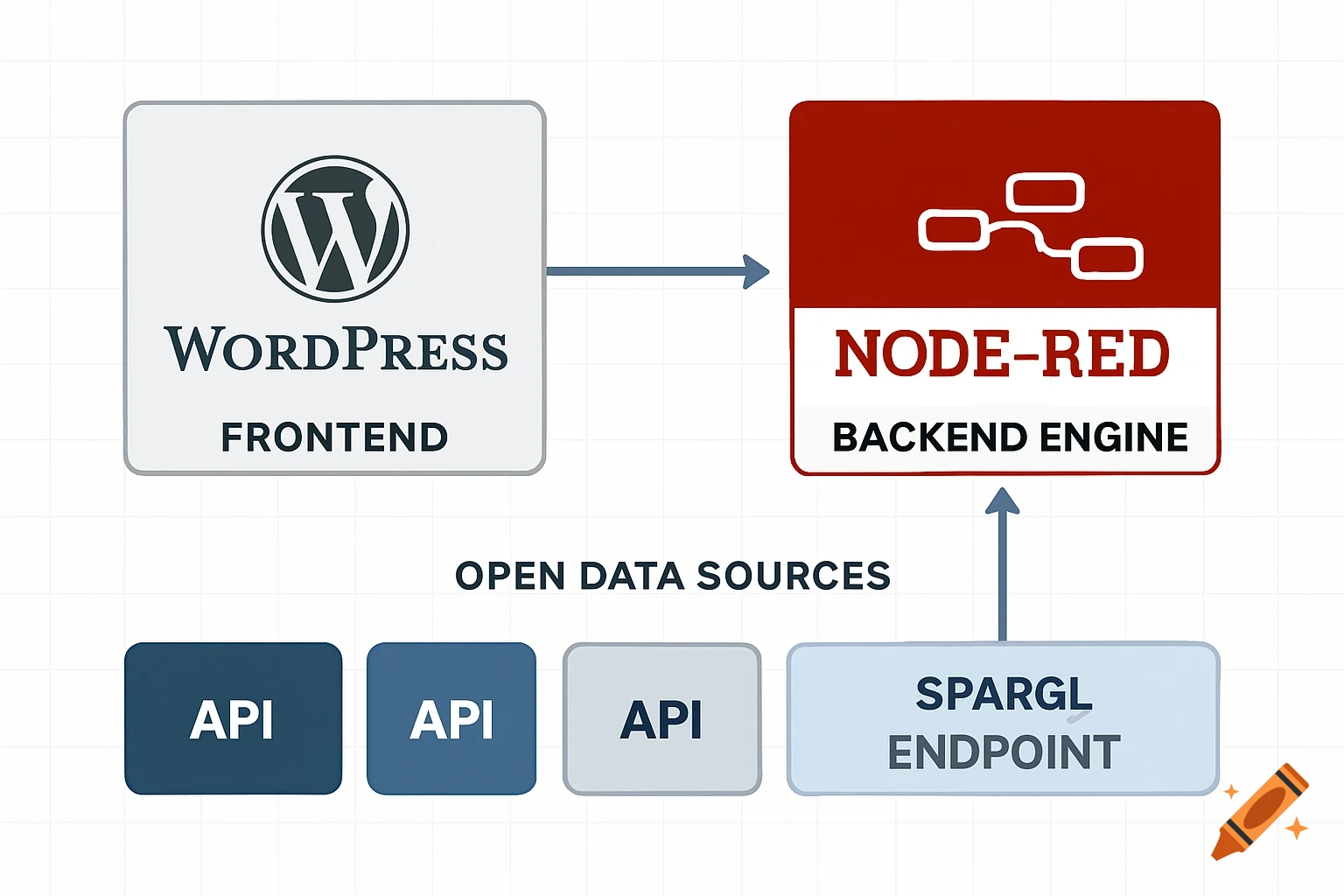
A split diagram illustrates normal DNS resolution on the left (green) and malicious DNS tunneling on the right (red) with network icons and data flow.
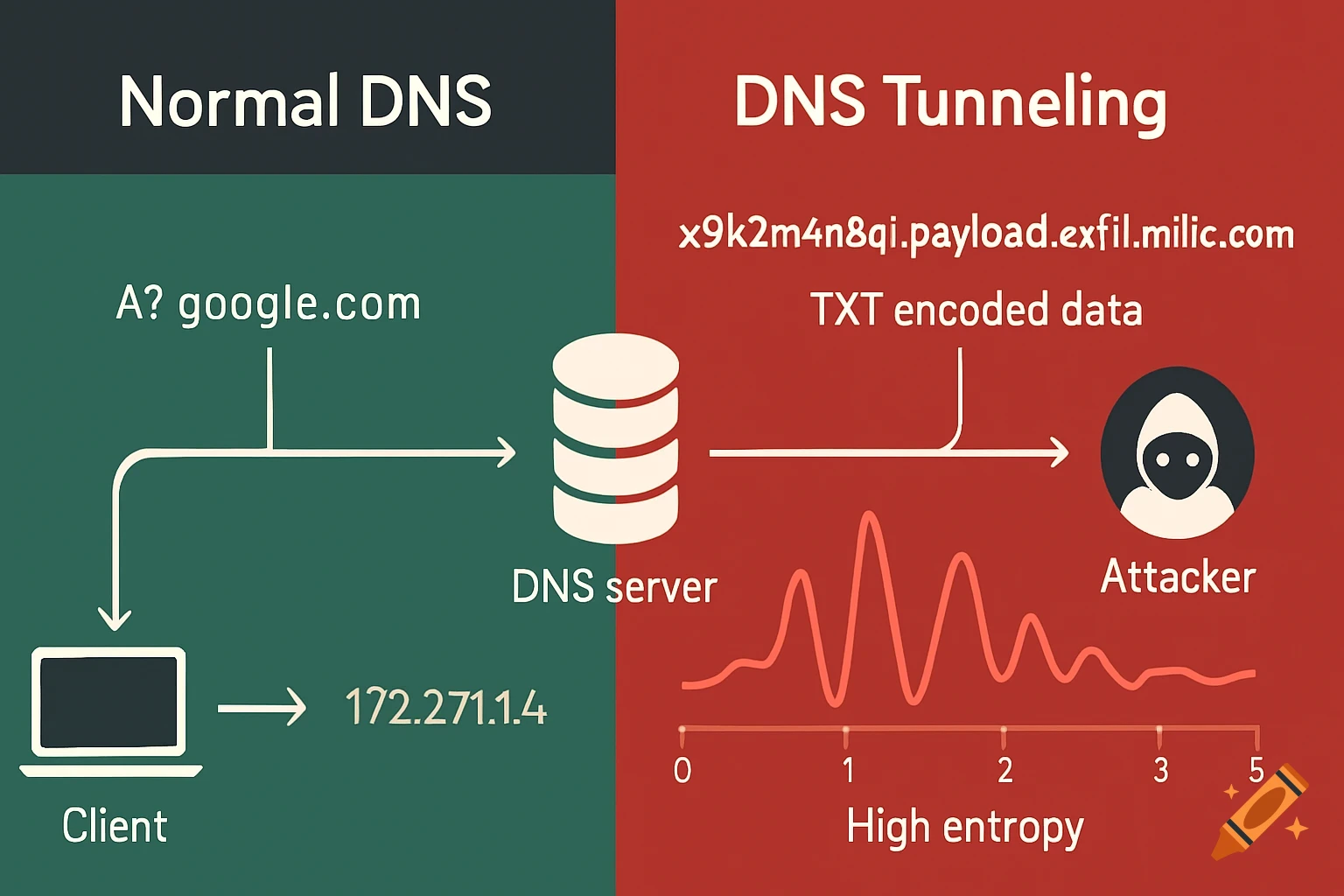
A split-panel technical cybersecurity diagram comparing normal DNS traffic (left) and malicious DNS tunneling (right). Left side: clean, simple DNS query 'A? google.com' resolving to a standard IP like 142.250.185.206, with short subdomains and low entropy. Right side: long, random-looking subdomain like 'x9k2m4n8q1.payload.exfil.malicious[.]com' sending encoded data via TXT record, with high entropy visualized as a red waveform or meter (0–5 scale). Include labels: 'Normal DNS' (green background) and 'DNS Tunneling' (red background). Use flat vector style, dark background, clear sans-serif font, and network icons (client, DNS server, attacker). Avoid photorealistic elements—focus on schematic clarity. image is for 16:9 so fit to 16:9 and have border See more